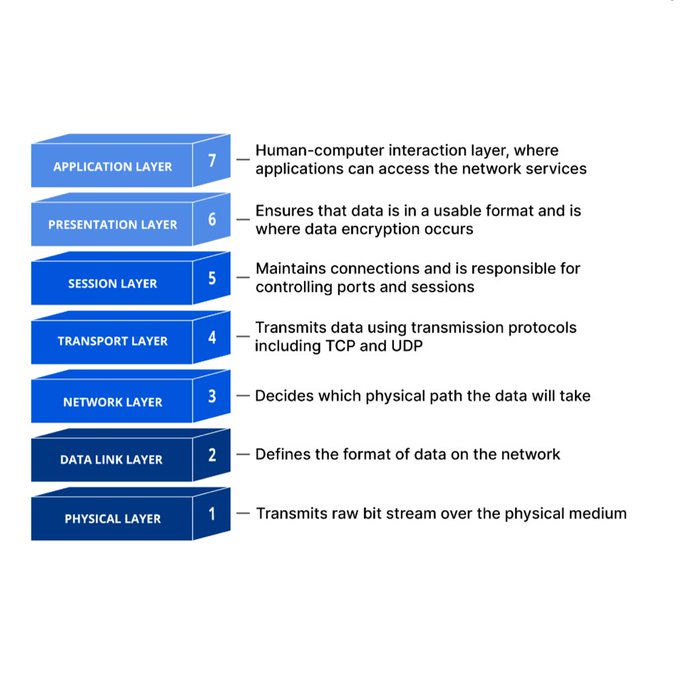
The firewall Should be at Layer 7 not 6
After being constrained by the limitations of the Man-on-the-Side (MoTS) strategy, which primarily allows passive observation of data, Pakistan’s spying agencies are likely looking to step up their game. To effectively intercept encrypted traffic, they may now be turning to a more invasive tactic: Man-in-the-Middle (MiTM).
Understanding Man-in-the-Middle (MiTM)
The Man-in-the-Middle (MiTM) strategy is far more aggressive than MoTS. In this approach, the spying agency positions itself directly between your device and the internet, often within the infrastructure of Internet Service Providers (ISPs). By doing so, they can intercept, alter, or even redirect your internet traffic. This method is not just about observing data as it flows by but actively engaging with it, allowing the agency to potentially decrypt secure communications, inject spyware, or manipulate the data stream to serve their purposes.
1-Click & Zero-Click Spyware
To enhance their surveillance capabilities, agencies may also deploy 1-click or Zero-click spyware:
- 1-Click Spyware: Requires the target to click on a link or download a file to activate the spyware. This approach is more traditional and relies on social engineering tactics to trick the user into initiating the attack.
- Zero-Click Spyware: Far more sophisticated, this type of spyware doesn’t require any interaction from the target. It can exploit vulnerabilities in the device’s software to gain access silently. This makes it particularly dangerous, as the user may have no indication that their device has been compromised.
Implications for Privacy
The shift from MoTS to MiTM, combined with the deployment of advanced spyware, represents a significant escalation in surveillance tactics. It allows agencies not just to observe but to actively manipulate the data, potentially bypassing encryption and accessing private communications without the user’s knowledge. This strategy, commonly used in other countries, could severely undermine digital privacy in Pakistan.
Understanding SSL Spoofing (HTTPS Hijacking)
SSL Spoofing is a sophisticated attack where attackers intercept and manipulate encrypted traffic between a user’s browser and a website. Here’s how it works:
- Accessing a Secure Site:
- You attempt to visit a secure website (e.g.,
https://xyz.com), expecting a secure connection.
- You attempt to visit a secure website (e.g.,
- Browser Expectations:
- Your browser expects a secure and encrypted connection with a valid SSL/TLS certificate.
- Interception by Attacker:
- An attacker, such as a government agency controlling network infrastructure, intercepts the connection. They might redirect traffic to an unencrypted HTTP page.
- Redirection to Unencrypted Page:
- During this brief redirection to an HTTP page, malware or spyware can be injected into your device using zero-click exploits, which don’t require user interaction.
- Vulnerabilities:
- Modern browsers warn users about unencrypted HTTP sites. However, outdated systems may be more vulnerable to such attacks.