Technology & AI
Fiber Wall or Firewall – A Comprehensive Guide: Understanding and Protecting Against SSL Spoofing and Network Surveillance

Deep Packet Inspection (DPI): Challenges and Solutions
Deep Packet Inspection (DPI) is a technique used to analyze and intercept data packets as they traverse the internet. While DPI on unencrypted HTTP traffic is relatively straightforward, the rise of HTTPS encryption presents a significant challenge for surveillance efforts.
DPI on Unencrypted (HTTP) Traffic
DPI on HTTP traffic is less complex because the data is not encrypted. This allows for easy inspection of the content of each packet, enabling agencies to monitor, analyze, and potentially manipulate the data being transmitted.
DPI on Encrypted (HTTPS) Traffic
The shift to HTTPS across websites globally has significantly increased privacy and security. HTTPS encrypts the data being transmitted, making it much harder for third parties to access or inspect the content of these communications. This encryption presents a major obstacle for DPI, as agencies cannot easily read or analyze encrypted data.
PTA’s Dilemma and Response
Given the widespread use of HTTPS and other encryption methods, the PTA faces a substantial challenge. Here’s how they might be addressing this issue:
- Inability to Decipher Encrypted Content: The PTA’s ability to perform DPI is greatly diminished when faced with encrypted traffic, such as communications on WhatsApp or other secure platforms. Without the encryption keys, decrypting this data is nearly impossible.
- Malicious Spyware Deployment: To overcome the limitations posed by encryption, there is a growing reliance on deploying malicious spyware directly onto devices. This approach bypasses encryption by allowing the spyware to access data before it is encrypted or after it has been decrypted by the user’s device.
The Strategic Shift
The need to install spyware on every device highlights a strategic shift from network-level monitoring to device-level infiltration. This method ensures that even encrypted communications can be accessed, making it a potent tool for comprehensive surveillance despite the challenges posed by encryption.
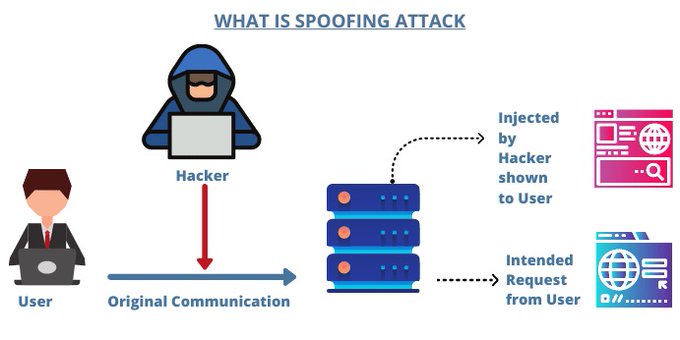
Zero-Click Spyware: The Next Level of Espionage
Zero-Click Spyware represents a highly sophisticated and invasive method of surveillance, where spyware is installed on a device without any interaction or awareness from the user. This technique is particularly concerning due to its stealth and effectiveness.
How Zero-Click Spyware Works
- Exploiting Vulnerabilities: Zero-Click spyware often leverages vulnerabilities in device software or web protocols. By exploiting these weaknesses, the spyware can be installed silently, without requiring any action from the user.
- Automatic Installation: The spyware may be delivered through various means, such as malicious websites or through compromised network infrastructure. Once the device accesses these sources, the spyware is installed automatically.
- Invisible to the User: Since no user interaction is required, the target remains unaware of the spyware’s presence. This allows for continuous and discreet monitoring of communications, data, and activities.
Connection to Recent Telecom Network Injection
The recent disruptions in Pakistan’s telecom networks could potentially be linked to the deployment of Zero-Click spyware. Here’s how these events might be related:
- Network-Level Exploits: If the telecom network has been compromised, it could be used to deploy spyware directly to devices connected to the network. This aligns with the hypothesis that the recent disruptions are not just technical failures but part of a broader espionage strategy.
- Enhanced Surveillance Capabilities: The ability to silently install spyware without user interaction would significantly enhance surveillance capabilities, making it possible to monitor encrypted communications and other secure data without needing to bypass encryption directly.
Exposing the Trickery
Unveiling Zero-Click spyware involves highlighting the methods and technologies used to exploit vulnerabilities:
- Detailed Technical Analysis: Investigating how these vulnerabilities are exploited and the techniques used for automatic spyware installation is crucial for understanding and mitigating these threats.
- Public Awareness and Advocacy: Raising awareness about the existence and risks of Zero-Click spyware helps individuals and organizations take preventive measures and advocate for stronger security measures.
Overall, Zero-Click spyware represents a significant threat due to its ability to bypass user defenses and operate unnoticed. The recent network issues in Pakistan may indeed be indicative of such advanced surveillance tactics in play.